
Latest Version: 3.3
What is Md5Checker?
C, -check check MD5 sums against given list -t, -text read files in text mode (default) Mac. Using Terminal in Mac Applications, Utilities: 1. Open Terminal 2. Type openssl md5 filename Or download and use third-party MD5 tool: MD5 for Mac (Calculate & compare MD5 checksums) MD5 is a utility that lets you create and compare MD5 checksums.
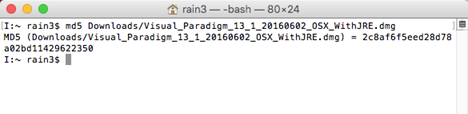
Nov 30, 2016 Checking the MD5 Checksum of a file ensures the file you are downloading is not corrupted and you are getting exactly what you are expecting. To check the MD5 using Terminal on a Mac is extremely simple. Open Terminal; Type md5 and hit the SPACE button; Drag the file you have downloaded into the Terminal Window. MAC Address or media access control address is a unique ID assigned to network interface cards (NICs). It is also known as a physical or hardware address. It identifies the hardware manufacturer and is used for network communication between devices in a network segment. MAC Address usually consists of six groups of two hexadecimal digits.
Md5Checker is a free, faster, lightweight and easy-to-use tool to manage, calculate and verify MD5 checksum of multiple files/folders (Screenshots):
- Calculate and display MD5 checksum of multiple files at one time.
- Use MD5 checksum to fleetly verify whether files have been changed.
- Load, save, add, remove and update MD5 checksum conveniently.
- It is about 300 KB and does not require any installation (portable).
What is MD5 checksum?

MD5 checksum (MD5 hash) is a type of digests of files. It will become totally different if any modification has been made to the file, even a byte.
Why should I use Md5Checker?
- To verify the integrity of downloaded files: With Md5Checker, user can calculate MD5 checksum of downloaded files and compare them with provided when downloading via HTTP, FTP, P2P, etc.
- To detect unknown viruses: Only-for-existing-viruses DB based anti-virus programs can rarely detect all emerged new (i.e. not in the DB) viruses in time. As a supplement, Md5Checker checks whether files are original. By that user can detect any change of file including virus infection.
- To make sure that the installation files are secure: System will be re-infected by viruses time and again while reinstalling software if the installation file had been infected. To avoid this, Md5Checker user can calculate and save the MD5 checksum right after downloaded/copied installation files, i.e. make sure these files are original (This step can be skipped if there are MD5 checksum downloaded/copied along with these files), and verify these files again upon using them.
- To make sure that files in a removable storage device are secure: In order to avoid bringing in viruses from using the removable storage device, Md5Checker user can calculate, save MD5 checksum in advance and verify files afterwards in the device. It is also a good idea to copy Md5Checker into the device to be able to check files anywhere and anytime. Note: Don’t forget to check the copied Md5Checker.
- To check out the security status of the system: It will indicate that the system was infected if the MD5 checksum of one executable file was changed without any action.
- To find out the virus source: It will indicate that one executable file is the virus source if the MD5 checksum of other several executable files have changed unexpectedly after executed this file.
- To calculate MD5 checksum for publishing: File distributors and software authors can use Md5Checker to calculate MD5 checksum of their files and publish them on the website.
This MD5 hash generator is useful for encoding passwords, credit cards numbers and other sensitive date into MySQL, Postgress or other databases. PHP programmers, ASP programmers and anyone developing on MySQL, SQL, Postgress or similar should find this online tool an especially handy resource.
What is an MD5 hash?
Md5 Hash Generator
An MD5 hash is created by taking a string of an any length and encoding it into a 128-bit fingerprint. Encoding the same string using the MD5 algorithm will always result in the same 128-bit hash output. MD5 hashes are commonly used with smaller strings when storing passwords, credit card numbers or other sensitive data in databases such as the popular MySQL. This tool provides a quick and easy way to encode an MD5 hash from a simple string of up to 256 characters in length.
MD5 hashes are also used to ensure the data integrity of files. Because the MD5 hash algorithm always produces the same output for the same given input, users can compare a hash of the source file with a newly created hash of the destination file to check that it is intact and unmodified.
Wedge Computer Repair Columbia Sc
An MD5 hash is NOT encryption. It is simply a fingerprint of the given input. However, it is a one-way transaction and as such it is almost impossible to reverse engineer an MD5 hash to retrieve the original string.
